Twitter is Insecure by Design - Just Don't Tell the President
Twitter is out-of-step with other leading websites with a flawed implementation of two-factor authentication
Twitter’s security model is horribly flawed
As we all get a bit more security and privacy conscious, things like two-factor authentication and security keys are starting to come into view. Two-factor authentication is now a core part of the login options of most grown up websites, Twitter being one of them.
When we enable two-factor authentication we specify an additional method of identification beyond just our password. In the olden days, the second authentication factor of choice was the SMS message. This is out of favour these days because of a cybersecurity vulnerability called ‘SIM-swap’ attacks. Nowadays we favour smarter solutions – the smartest of which is a security key – a purpose-built hardware device that we take with us and plug into our computer to prove this it really is us that is logging in and not some random attacker.
Yubikey is the Rolls Royce of security keys - let’s us it to lock down Twitter
I’m a big fan of anything that improves security and privacy, and so when I went to secure my Twitter account with the new Yubikey 5 NFC I was very disappointed to learn that Twitter doesn’t really support security keys. I kinda supports them. But not really.
Here’s the problem with trying to secure your Twitter account with a security key such as the Yubikey…
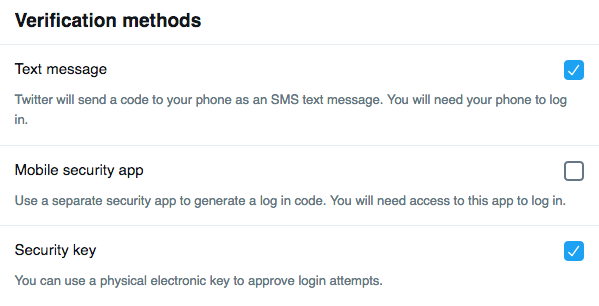
Twitter supports multiple forms of verification methods. YAY.
When you enable two-factor authentication (2FA) on your Twitter account, Twitter insists that you register your phone. OK. That’s standard. No problems there. This will wind up being the first type of two-factor authentication – SMS messages. Next, Twitter gives you the option of extending your two-factor authentication footprint to include a security key. Fantastic. Two methods of two-factor authentication are better than one - especially when that one is SMS. But this is where the problem starts.
Now that you’ve defined a security key on your account, you’ll want to disable SMS messages. SMS messages are a fundamentally insecure method of authentication because of the reason previously mention – SIM-swap attacks. So we don’t want anything to so with SMS authentication. We prefer security keys.
Twitter’s 2FA options include SMS. That is all.
Too bad. Twitter won’t let you disable SMS as an authentication method. Period. You can’t do it. Now, that wouldn’t be so bad if you could prioritise the security key authentication over SMS messages as your preferred method of two-factor authentication. But you can’t. SMS is the default and so even if you have a security key defined on your account, Twitter won’t use it. It’ll just send you an SMS authentication message automatically. And here’s the kicker. ..
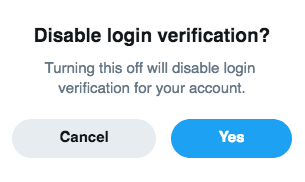
If you disable SMS authentication on Twitter you disable 2FA entirely. That’s rubbish.
Twitter 2FA - SMS or nothing
On the Twitter App 2FA=SMS
When you try and disable SMS as a method of two-factor authentication, it disables two-factor authentication ALTOGETHER! So even when you’ve gone to the trouble and expense of securing your Twitter account with a dedicated security key, your choices for two-factor authentication on Twitter are a) SMS authentication or b) Nothing.
And there’s more…
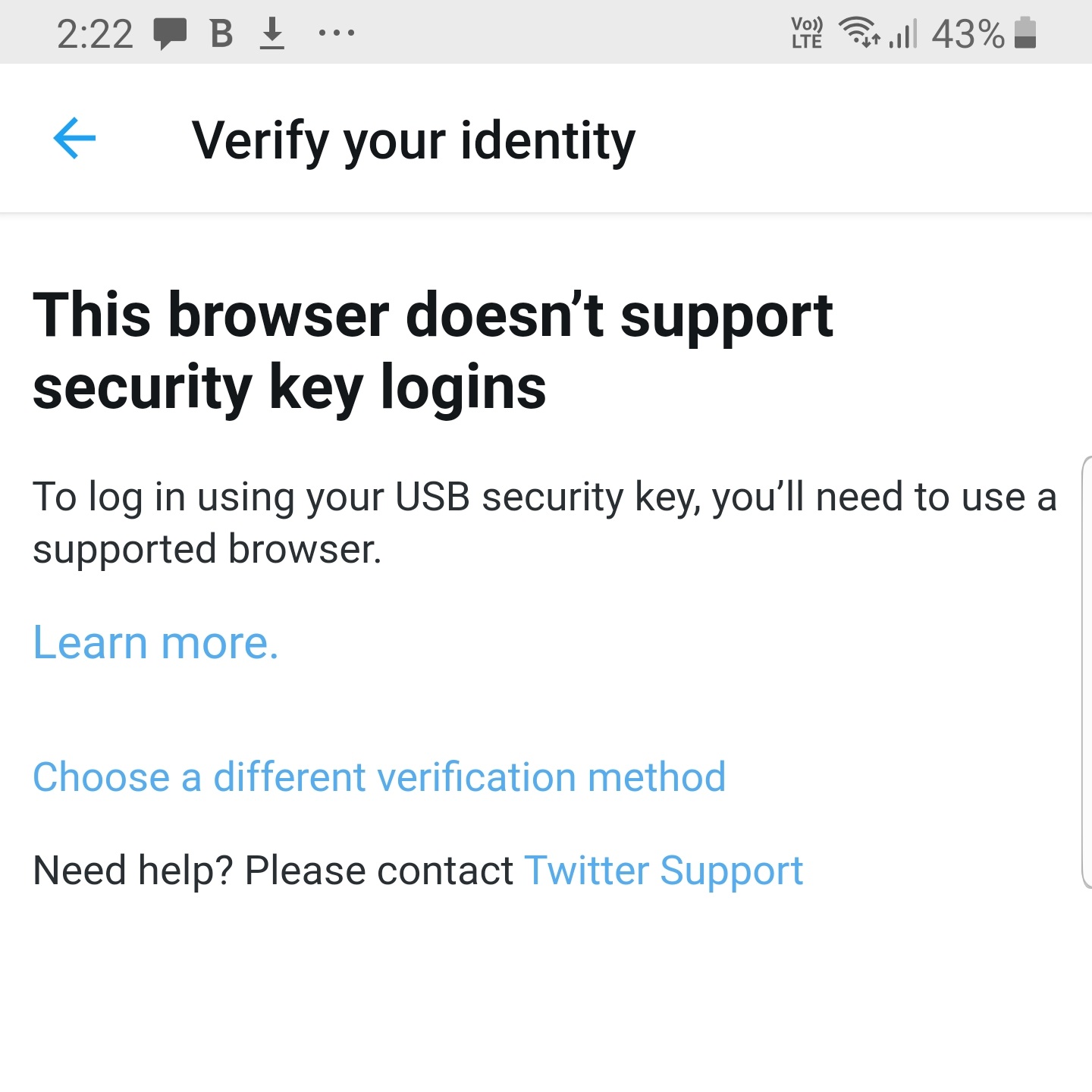
2FA on the Twitter App
The Twitter Mobile App doesn’t support security keys at all. Not even a little bit.
Twitter - insecure by design
This is why Twitter is insecure by design. I’m surprised that the President’s security people let him anywhere near it. If that account gets hacked, God save us.